


In our modern world, most people are using cyberspace for many things like shopping, social media, playing games, watching movies, even paying today's bills, which has many potential traps. In this tutorial, we are going to learn about the internet and the security measures for using the internet safely and the need for the security of the internet.
Security means protecting something from unauthorized or malicious attacks. Here also in the same definition, the term cyber security means protecting the systems such as computers, mobile, or any other devices or the data that is connected to the internet or inside the internet from malicious attacks.
Simply the term “cyber security” is formed by joining two words, which is “cyber” that means the internet that includes all the devices like computers, phones, routers, switches, and the data related to the internet and “security” means protecting them from the hackers or criminals who attack in cyberspace.
Therefore, as a definition, we can say “cyber security refers to a collection of principles or procedures which help to protect our information and the devices from all types of threats on the internet”.
Now we think about why I should be concerned about such types of threats and security, which is related to the internet? it is only for someone who is a software professional or someone who is working in cyberspace.
The answer is no. Every one of us is using the internet and the services that use the internet in all our day-to-day activities like social media, online transactions, online shopping, online bill payments, and more that we can’t explain. Most of our phones are always connected to the internet and we all are a part of cyberspace so we all need to know how to use this internet without having any threats.
The internet is becoming a dangerous place for all including organizations and persons. There are a lot of people and machines accessing the internet and all the systems connected to the internet are mutually connected, so we need to protect our valuable data from vulnerable attacks.
There are many reasons for that like
With all these methods, anyone who is able to use a system can learn these tricks and attack anyone who is illiterate about the internet.
What we can do to avoid such problems on the internet is to increase our knowledge about the internet or cyberspace. Making all the parts of the internet is not possible so we have to protect our networks and operating systems so that we can protect ourselves up to an extent. Now, cyber-attacks and hacking is one of the most important economic problems with international concern.
You can understand the current scenario from a simple graph given below.
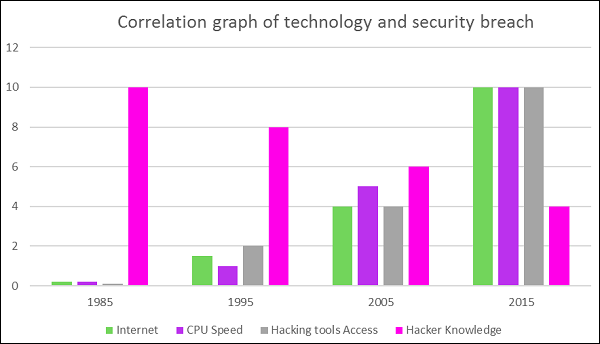
In cyberspace, there is a wide range of threats or attacks that involve the loss of confidential data, corrupting the data, financial loss, loss of control of a network, loss of accounts, and much more.
In general, cyber threats can be defined as malicious activity that is done by an individual or a group that results in loss or disrupts another person’s life or property.
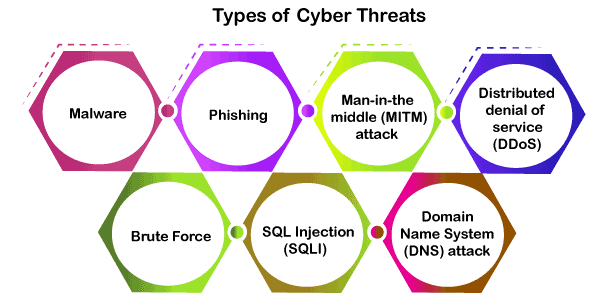
It is the most common threat or cyber-attack tool in cyberspace. It is a malicious program that is able to be installed in our system or the browser and cause damage to our system. We all have encountered malware attacks but were blocked by antivirus or some defender. Some of the common type of malware attacks are
1. Virus
2. Worms
3. Trojans
4. Spywares
5. Adware
6. Botnets
7. Ransomware
It is a type of cybercrime we all have encountered in our daily life in the form of emails, messages, or even phone calls. In this method, the sender seems to be from an authorized company like some financial institutions, call centers, PayPal, or other shopping sites, etc. Here they will send us some E-mails or messages with some links or pictures. If we click these links or pictures, that will direct us to their fraud websites, which are programmed to take our sensitive and secret data or even install some malware in our device. Once the hackers got our data or the malware installed they even can remote login to our device and can control it.
This is a kind of cyber-attack, which is not targeting the end-users. This cyber-attack will disrupt the working of a server and its functions. We know how the internet works like when a user requests some data from a server, the server sends the response with the data.
In a DDOS attack, the hackers are sending junk requests in large quantities to a server and making the server bandwidth filled, and making the server down temporarily. Finally, the server cannot able to handle a genuine request and we get a response as the server is down.
It is a type of cybercrime in which the hacker or a cybercriminal does an eavesdropping attack as the hacker intercepts the messages between the two persons and starts to involve in the conversations pretending to be a genuine user. Once they reach the middle of the conversations, they can get access to sensitive business data.
This a also called a trial and error method which is a cryptographic method mostly to extract the password or pin or other sensitive information. In this method, the hacker will try all the possible combinations for a password until the real one is obtained.
DNS is related to the website and its address; we are typing the address of a website to reach that website all the part of DNS. In this attack method, the hacker identifies some websites, which have some errors in their DNS and uses that website to divert the users to another malicious website to extract the information from the users.
There are much more attacks that will be detailed in the coming tutorials.
The main objective of cyber security is to provide security to the confidential and sensitive data and the devices, which are accessing cyberspace. In general, we can rely on three principles, which are needed to assure the security of the internet.
These three principles are called the CIA triad. This model is helpful to provide an organization with some rules or guidelines to protect their data and the resources in the internet. Let us discuss each of these principles in detail
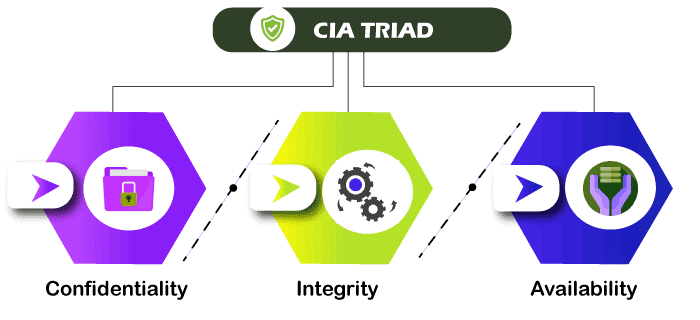
Confidentiality refers to the level of privacy for data. Confidential data means highly important data that needs to have high privacy which means we have to secure the data from unauthorized access. We need to block unauthorized access to the data. Data encryption is one of the methods used to make sure confidentiality.
Integrity means protecting the data and the sensitive content from unauthorized modifications. It is important to keep the data secure without giving a chance to modify the data purposefully or accidentally. We also have to keep some measures to revert the original data if some modification occurs to keep the data genuine.
We said the data must be secure and genuine but the important thing is to make the data available for authorized or genuine users. That is done in availability that keeps the authorized users are not being blocked by malfunction or accidental.
Cyber security is a vast area and each company or an organization has different areas and data and different combinations of data and systems to protect from the cyber criminals. Therefore, we have different types of cyber security as below
Etc and we detail each of them in coming tutorials