


We know we are living in a digital world where almost all our daily activities depend on the internet and electronic devices such as e-shopping, mobile devices, social media, online banking, and many more. This dependency can lead to illegal hackers and cybercriminals opening a way to steal your information and identity. Now, these illegal activities have grown into a fearful crime world.
A cyber-attack can be defined as an illegal attack or accessing of a computer or a network and stealing the data from it or trying to destroy that system or network with the help of a computer worm or malware. This kind of attack leads to loss of information or identity or even money can be referred to as cybercrime and the person who is behind a cybercrime is called cyber-criminals.
Broadly the cyberattacks can be divided into two types which are based on the impact of the attack that are
As the name suggests, web-based attack is attacks that target websites and network components. It can make an impact on any website or web application directly or indirectly. Some of the web-based attacks are
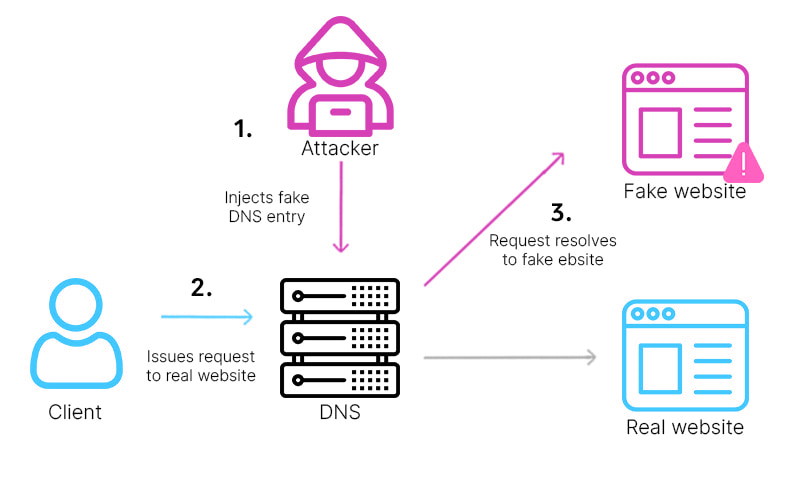
DNS is called Domain Name Server, which helps the request from the user to reach the correct IP address of the website. DNS spoofing is a method where the hacker adds data to the Name server cache that diverts the user requests to a wrong IP address or a wrong system.
This kind of attack diverts the traffic to a wrong server or a system and it can stay on the Name server cache without being caught for a long time.
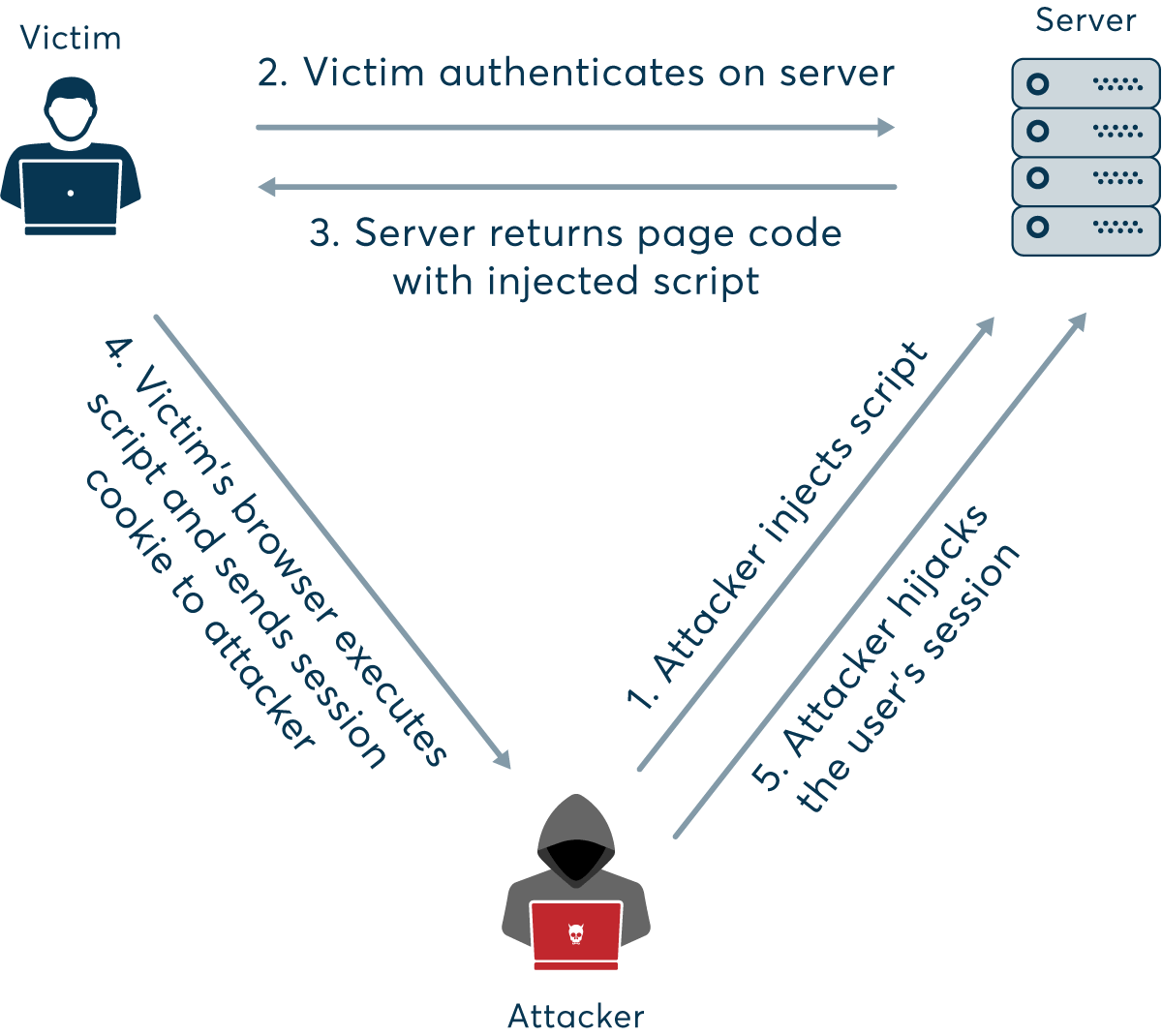
It is a type of attack on a user session to get all the data about that user. Websites will make cookies that store some of the important information about the user and stealing those cookies will make the hacker get all the user data.
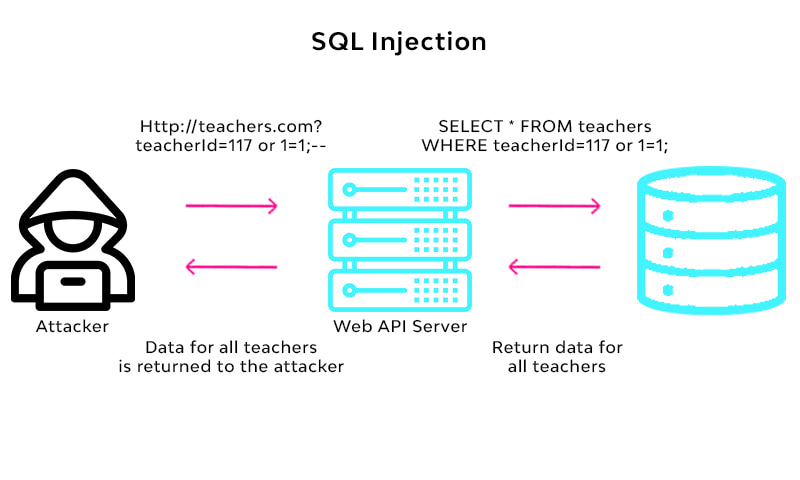
It is a different kind of attack on a website where the hacker will inject some codes that can able to manipulate the website database and the hacker can able to get all the information from that website database.
Example: SQL Injection, XML injection, etc
The Internet is our daily companion now, almost all of us are using the internet for one or another need, almost all day. While you are surfing the internet have you ever seen something like a popup showing your computer locked, or infected, or some dangerous threat found, like that? It is called Scareware. It also has a button as a remedy like downloading some software or asking for a payment. If you click such a download button a malicious program gets downloaded and installed called scareware in your computer that makes your computer locked until some ransom is paid or even steals data from your computer.
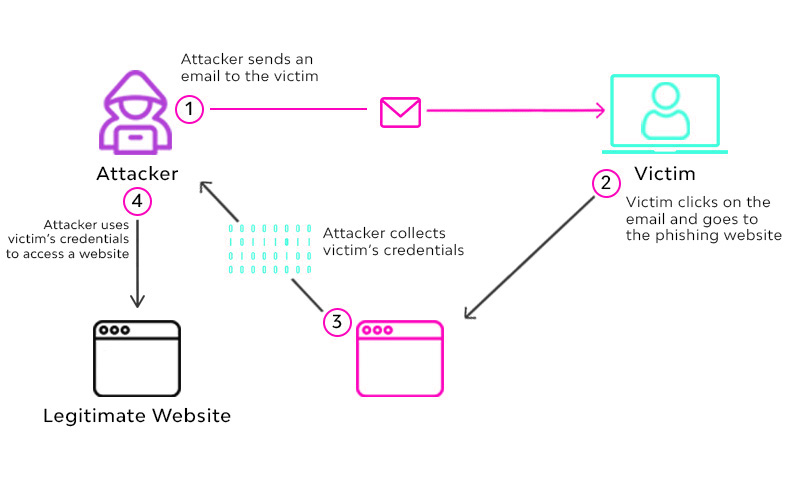
Phishing is a type of cyber-attack that aims to steal the user's sensitive information like login information or the bank transaction details or credit card details. It is done usually through email where the hacker sends an email that will appear to be from a genuine source. It was also used to install the malware in victims' computers.
We already heard about the need for creating a strong password that includes numbers, special characters, etc. that is to regulate this type of attack called brute force. In a brute force attack, the hacker tries many combinational guesses until he finds the correct credentials. This method is also used to crack encrypted data.

Denial of services or Dos attack is a common type of attack that a cyber-criminal try to make a server down by sending a huge amount of junk requests (traffic) to that server until the server is able to process the request.
Once the server is exhausted the genuine users are also unable to reach the server and it destroys the network. In simple words, this attack is denying a service from the server to a genuine user. It can be three types
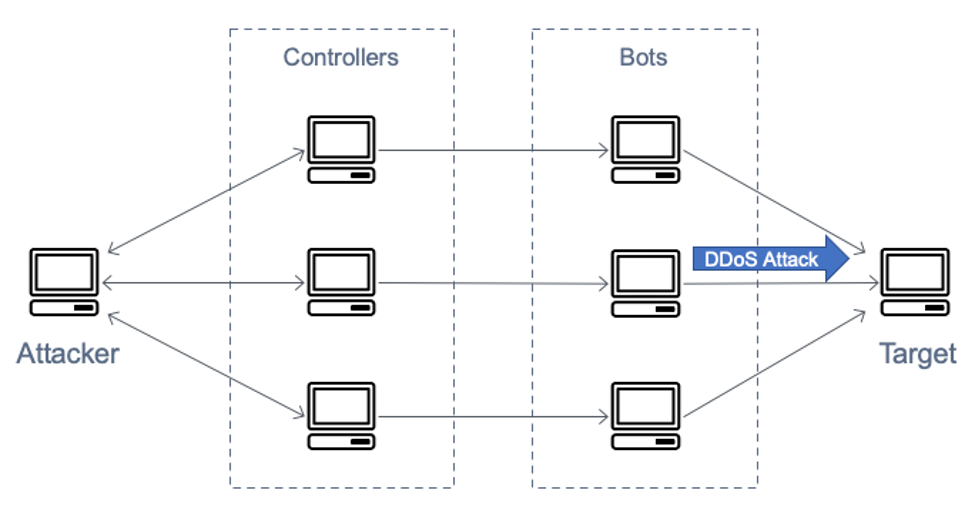
7.1 Volume Attacks: Hackers send huge traffic to make the bandwidth of a website get exhausted.
7.2 Protocol Attacks: this type of DOS attack makes the server resources exhausted as it consumes the original server resources without any need.
7.3 Application Layer attack: Its main aim is to make the webserver
Every server has some pages that will not be accessible to the public. In URL interpretation the hacker changes the URL and makes the server deliver the secret pages to the user.
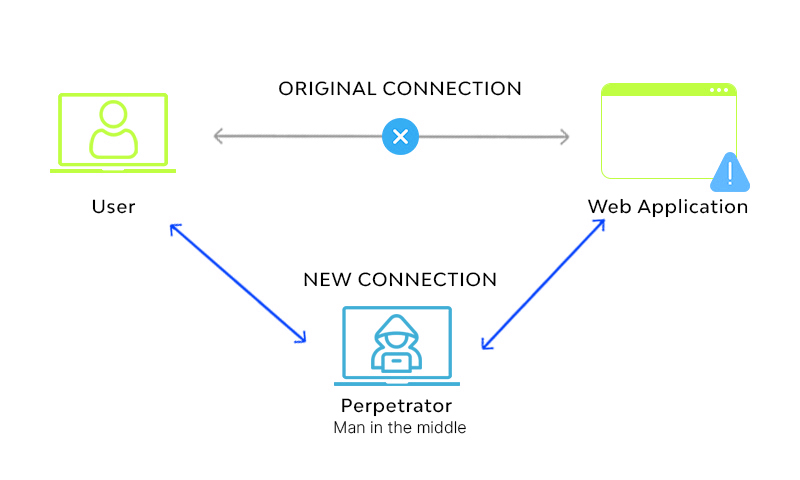
As the name suggests the hacker intercepts a connection and acts as an intermediary who is between a user and a server. The hacker is able to read and modify all the messages that the user and server communicate.
The Internet is full of ads and that is the major revenue source of many websites running in cyberspace. But some criminals make some malware that forces the user to show the ads and redirect the user to an ads page or a product page.
The above attacks are based on a network and the internet. Now there is another type of attack, which targets the system and its resources.
As the name suggests, it is a bit of computer code that can able to travel through the computer system and spread without the user knowledge and able to self-replicate and it contains an executable code snippet that will be capable of destroying a system or able to steal some data from the system that is infected. Some of the world’s dangerous viruses are
Spywares are some malicious program codes, which are being installed in the target system without the user's knowledge that is able to steal the sensitive information from that system and send that information to a remote server. Usually, the browsing pattern and interests of a user are sent to the server.
More dangerous spyware includes keyloggers, which can able to access our password that we type on our keyboard and send the data to the server. Usually, malware will get installed while installing freeware that we download from an unknown source.
Worms are a kind of virus that aims to steal sensitive information or to destroy a network or a system. Unlike the virus, a worm does not need any human activity to spread from one infected system to another system in a network. Worms replicate and spread through the network using email or the loopholes in an operating system. It also uses the resources of the network or a system making it slow or unusable for authentic users.
Trojan horses are an old war structure that hides the folders inside a huge horse that has a backdoor and it attacks from inside the enemy territory. Like that Trojan horse is a code snippet that pretends to be authentic software from an authentic source but can able to make unexpected changes to the host system. Trojans will run as a normal program but it will destroy the data in the host system and make it vulnerable to attack like opening a backdoor for a remote system to control this host system.
Trojans can able to make many host computers to be controlled by a master computer and it forms a network of such zombie computers. Trojans are less dangerous than worms and viruses because they cannot replicate or spread to another system in a network.
It is a method of bypassing an authentication process, it is usually done by the developers to access some applications. But cybercriminals use this method to crack many paid software, even the operating systems.